A phishing campaign targeting Indian government entities and the defense sector has been identified, deploying Rust-based malware for intelligence gathering. Detected in October 2023 and named Operation RusticWeb by enterprise security firm SEQRITE, the campaign employs new Rust-based payloads and encrypted PowerShell commands to exfiltrate sensitive documents to a web-based service engine.
Tactical connections have been uncovered between this operation and groups like Transparent Tribe and SideCopy, both associated with Pakistan. SEQRITE previously detailed campaigns by SideCopy involving trojans such as AllaKore RAT, Ares RAT, and DRat targeting Indian government bodies.
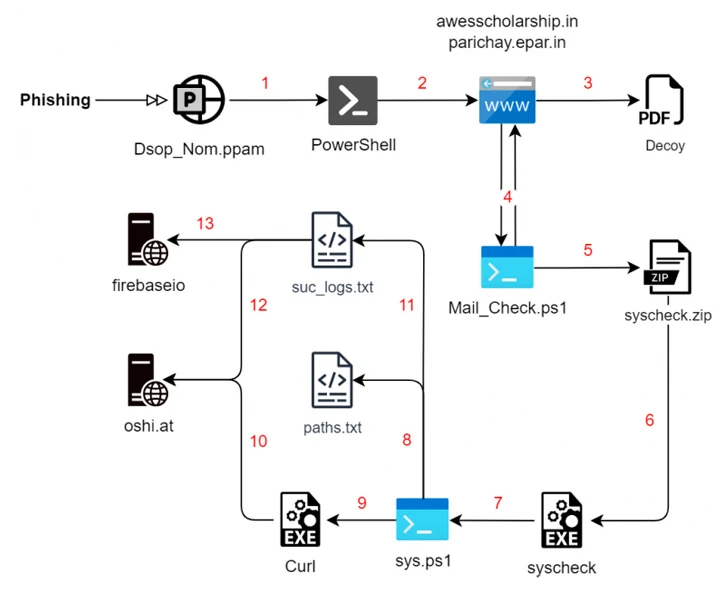
Recent attack chains, documented by ThreatMon, utilize decoy PowerPoint files and specially crafted RAR archives for malware delivery. The SideCopy APT Group’s infection chain involves multiple orchestrated steps, starting with a phishing email leveraging social engineering techniques. The malware drops Rust-based payloads to enumerate the file system while displaying decoy files.
In another infection chain identified in December, a similar multi-stage process is employed, but the Rust malware is replaced with a PowerShell script. The final-stage payload is launched via a Rust executable named “Cisco AnyConnect Web Helper,” uploading information to the oshi[.]at domain.
Security researcher Sathwik Ram Prakki suggests a potential link to an APT threat due to similarities with various Pakistan-linked groups. This disclosure follows Cyble’s discovery of a malicious Android app used by the DoNot Team, an Indian-origin nation-state actor known by names like APT-C-35 and Origami Elephant. The app targeted individuals in the Kashmir region, showcasing the group’s persistent efforts to refine tools and techniques for ongoing threats.
